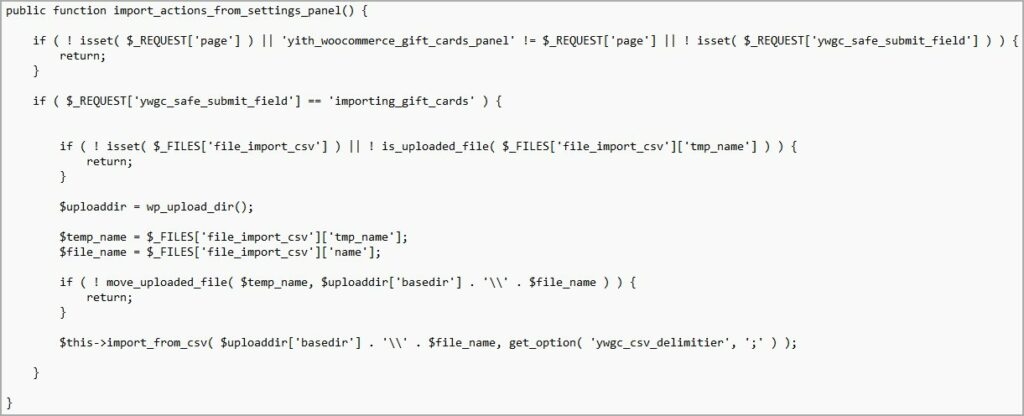
The vulnerability which is being exploited is traced as CVE-2022-45359 (CVSS v3: 9.8), allowing the hackers to upload files to unprotected websites, which include web shells that give full access to the website. The vulnerability CVE-2022-45359 was informed to the public on 22 November 2022, affecting all versions of the plugin till v3.19.0, and the critical flaw was addressed in v3.20.0 although the people behind the plugin have already released the v3.21.0, which the people using the Gift card premium plugin are recommended to update. With that being said, many people have not upgraded to the latest version, hence using the vulnerable version, and the hackers have already built a working method to attack them. As per the security pundits at Wordfence (a WordPress plugin for security), the exploit is already underway, with the attackers already utilizing the vulnerability to obtain code execution, apply backdoors on the websites, and start the takeover attacks. The people at Wordfence reserve engineered an exploit that was used by the hackers in the attacks, and they found that the vulnerability was in the plugin’s “import_actions_from_settings_panel,” a function that runs on the “admin_init” hook. Also, this function doesn’t perform CSRF (Cross-Site Request Forgery) or capable checks on vulnerable versions. Read: Godfather Android Malware Stealing Bank Websites & Crypto Exchanges’ Data Well, these two issues make the attackers send POST requests to “/wp/admin/admin-post.php” using the relevant framework to upload a malicious PHP executable on the website. Furthermore, it is trivial for an attacker to send a request containing page parameters set to yith_wocommerece_gift_cards_panel_a_ywgc_safe_submit_field set to importing_gift_cards and a payload in the file_import_csv file parameters added Wordfence. The malicious requests arise on logs as unexpected POST requests from an unknown IP address, which signals the website’s owner that they are under attack. These are the following files that Wordfence saw. The experts at Wordfence believe that the attacks that majority of the attacks happened in November before the plugin admin could path the critical flaw. In addition to this, the second wave that happened was observed on December 14, 2022. This IP address 103.138.108.15 was the important source of the attack, launching 19,604 exploitation attempts at 10,936 websites, and the second IP address used is 188.66.0.135, which performed 1,220 against the 908 WordPress websites. The exploitation attempts are still underway, so users of the YTTH Gift card premium plugin are recommended to update to the latest version, i.e., v3.21.0, to avoid exploration of their websites! Read: Muddy Water, a Hacker Group Used Compromised Corporate Emails for Sending Phishing Messages